The Cyberspace Administration of China (CAC) has introduced a new regime for cybersecurity reporting which took effect on 1 November. This comprises new Administrative Measures for National Cybersecurity Incident Reporting, accompanied with a Cybersecurity Incident Grading Guide (Reporting Measures). A dedicated reporting platform is now available for firms to facilitate online reporting.
The finalised Reporting Measures came in less than one week after Dior became the first foreign brand sanctioned for non-compliance with China’s cross-border data transfer requirements, following the company’s disclosure in May that a cybersecurity breach resulted in unauthorised access to customer data in China.
Organisations operating in China should take immediate action to assess their data breach reporting protocol and process, to ensure they meet the stringent reporting timeline in the event of a data breach.
Four-tier classification of cybersecurity incidents
Consistent with the original draft consultation, the Reporting Measures classify cybersecurity incidents into four tiers based on their impact on national security, social order, economic activity, and the public interest: “general (一般)”, “relatively severe (较大)”, “severe (重大)”, and “particularly severe (特别重大)”.
The Reporting Measures impose stringent reporting timelines and procedures for incidents classified as “relatively severe” and above. An incident may be considered “relatively severe”, for example, if it involves the loss, theft, tampering, or falsification of important data or a large volume of personal information that poses a serious threat to national security and social stability.
The Reporting Measures do not explicitly state whether “general” incidents require reporting. It remains unclear if these lower-level incidents are exempt or if they will be subject to a more relaxed reporting timeline pending further clarification from the regulator. In any event, organisations in regulated industries such as financial services must also pay attention to industry specific rules.
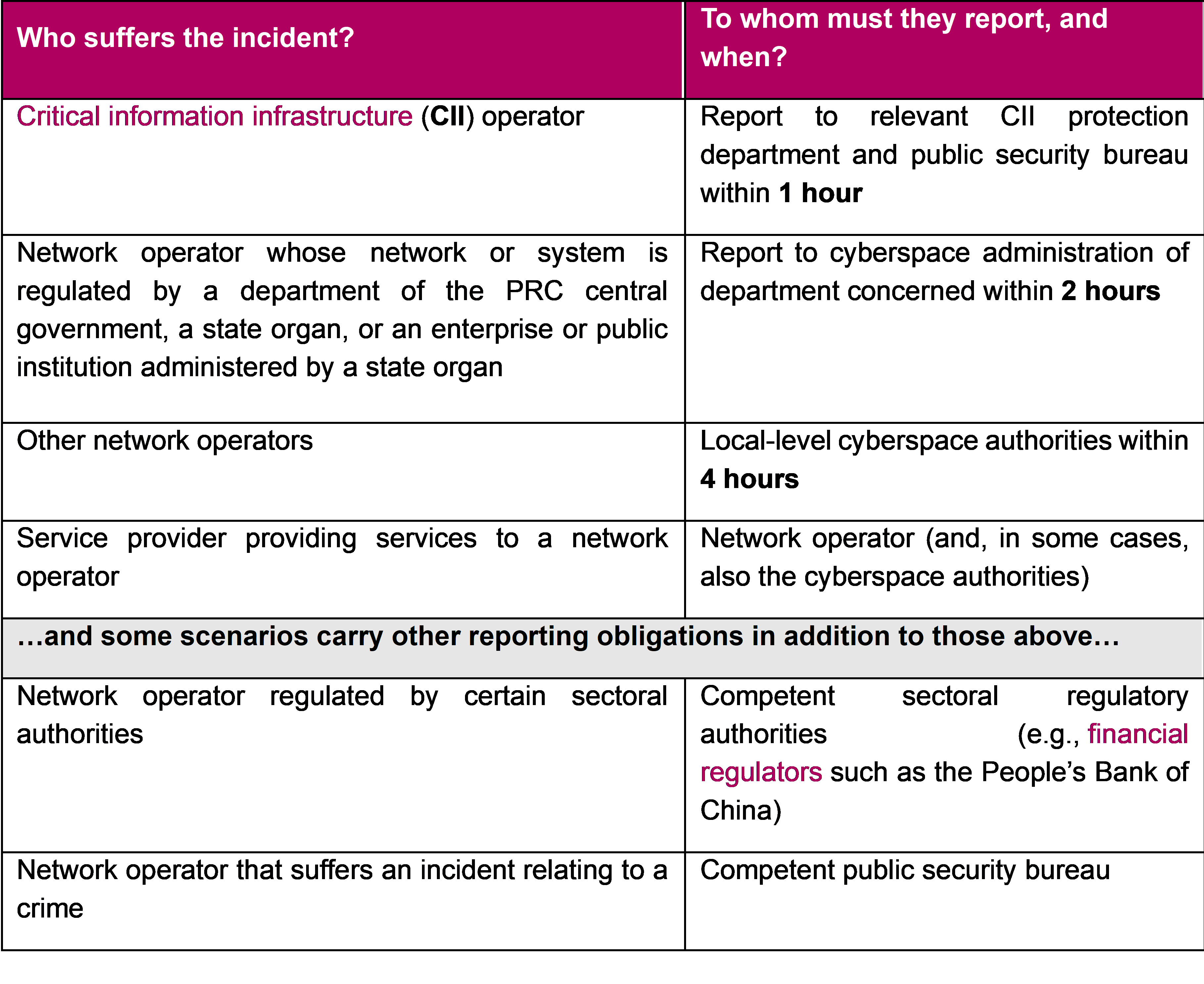
Who must report a cybersecurity incident?
This will depend on the nature of the organisations' business:
Network operator: The legal obligation to report rests with the network operator. This refers to the entity that builds, operates, or provides services through electronic networks within mainland China, and aligns with the definition of network operator used in the Cybersecurity Law. In essence, businesses operating in China will broadly be subject to these reporting requirements.
IT services providers: The Reporting Measures require network operators to contractually oblige their third-party vendors, such as cybersecurity service or system maintenance providers to notify them of any incidents promptly and provide all necessary assistance within the reporting process.
Overseas business: While the Reporting Measures do not explicitly create direct extra-territorial liability for offshore businesses processing data originated from China, overseas businesses may still be indirectly affected in several ways. For one thing, an offshore service provider may be contractually required to promptly report to its customers in China and assist them to fulfil their reporting obligations. In particular, offshore recipients are contractually bound to notify their Chinese partners of a data breach under the standard contractual clauses (SCCs). For another, although the use of “network operator” implies that the Reporting Measures’ primary jurisdictional scope remains consistent with the CSL—focusing mainly on networks within mainland China—given that the Reporting Measures implement the CSL, DSL and Personal Information Protection Law, offshore business can still be subject to the extra-territorial application of the PIPL.
This regime places increased importance on vendor due diligence and sound contractual governance. Multinational enterprises should carefully review their vendor contracts and incident response plans to ensure these obligations are clearly addressed and that their suppliers are prepared to meet the compliance requirements in practice.
To whom must reports be made, and when?
The Reporting Measures map out different reporting channels and the required timeline in the event of relatively severe, severe, or particularly severe:
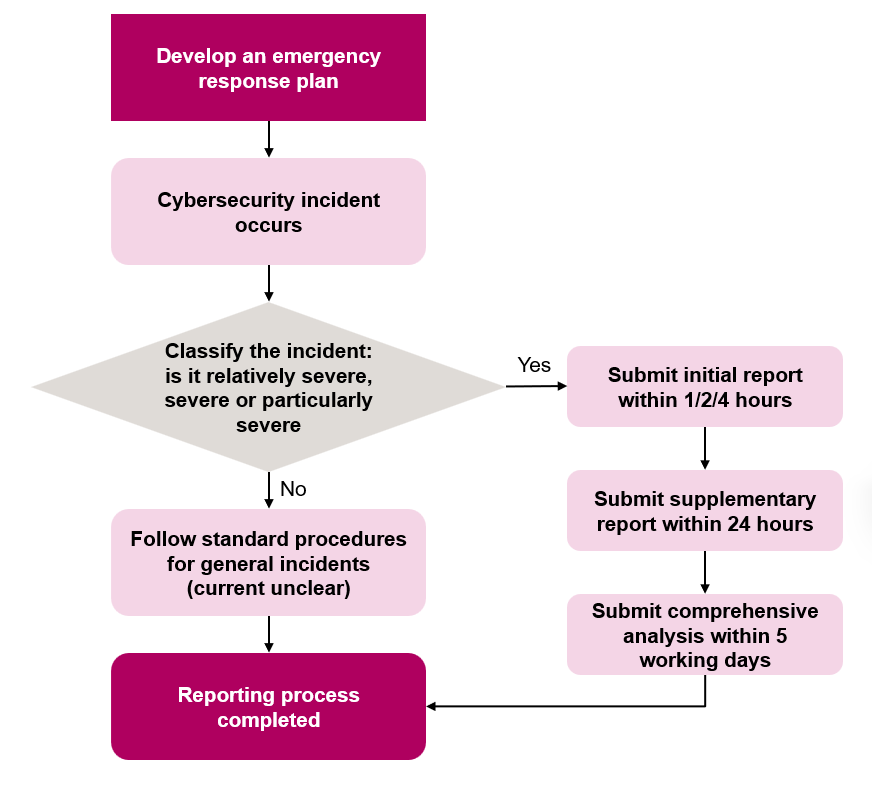
A reporting flowchart
Following the Guidelines’ grading criteria, in the event of any relatively severe, severe, or particularly severe cybersecurity incidents, network operators must operate according to the following procedures:
Are there benefits to reporting a cybersecurity incident?
Yes. The Reporting Measures has kept its position from the previous draft, where the liability of a network operator will be reduced or exempted at the regulatory authorities’ discretion, if the network operator adopts reasonable and necessary protective measures and timely reports incidents to the authorities.
To benefit from potential exemptions, organisations should establish a comprehensive cybersecurity handling and emergency response plan.
What’s next?
Industry and sector-specific reporting rules and guidelines: Financial institutions should also note the new People’s Bank of China cybersecurity reporting rules, effective 1 August 2025, which introduce very tight timelines. For significant incidents, these rules mandate a brief report within one hour and a detailed report within 24 hours, highlighting the need for rapid response capabilities. In parallel, a non-binding practice guide has also been released for generative AI services, outlining methods for incident classification and emergency response. Both developments highlight the growing regulatory focus on creating specific security frameworks for high-risk sectors.
Increased regulatory enforcement: Recent actions from regulators, such as the publication of typical enforcement cases in September 2025, signal a clear trend towards stricter enforcement of data security laws. This demonstrates that authorities are actively monitoring compliance and are prepared to penalise organisations that fail to meet their legal obligations. Additionally, the amendments to the Cybersecurity Law which will take effect on 1 January 2026 have further strengthened enforcement mechanisms and expand regulatory powers, underscoring the authorities' commitment to robust oversight.
Key takeaways for multinationals
In light of these developments, multinationals operating in China should take proactive steps to ensure compliance and mitigate regulatory risks, including:
Review and update incident response plans: Ensure existing incident response plans and policies are updated to reflect the latest Reporting Measures.
Strengthen vendor due diligence and contract management: Review contractual arrangements with external vendors. Contracts should clearly specify reporting timelines, notification obligations, and cooperation mechanisms, to facilitate compliance with the Reporting Measures.
By taking these measures, organisations can better position themselves to navigate China's evolving cybersecurity landscape.
As always, feel free to reach out if you have any questions.


/Passle/5c4b4157989b6f1634166cf2/MediaLibrary/Images/2026-01-28-11-42-24-951-6979f620da2c44bd51323e05.jpg)
/Passle/5c4b4157989b6f1634166cf2/SearchServiceImages/2026-02-26-09-59-52-439-69a019985e365c8f59bcd200.jpg)


/Passle/5c4b4157989b6f1634166cf2/SearchServiceImages/2026-02-26-11-29-56-314-69a02eb452230663c9b9705f.jpg)